Site Scan
Our security experts scan your website for malware to detect and determine the extent of the damage. Whether is a MySQL or JavaScript injection, a defacement, or hidden iFrames, we’ll find it if it is there.
Malware Removal
Our team of security professionals will remove the malicious code from your website’s files. Up to 10,000 core files. You’re in good hands once our squad is able to review your files and eliminate the problem.
Secure Website
Once the source of the hack is repaired, we will install security monitoring scripts and a firewall to keep your site secure. This will allow you to have peace of mind, knowing that your site is now a fortress.
Boost Performance
We work to improve your pagespeed and improve the performance of your website wherever possible. There are a number of performance improvements most sites are lacking, which can help it load faster.
Your WordPress site is hacked. Now what?
There are numerous reasons why your website got hacked or infected with malicious code. Common attacks involve installing malware, using brute force techniques to crack your login, exploiting plugin or theme vulnerabilities, defacing the site, creating sub-pages and redirects to sell counterfeit or illegal goods, and more.
Once you have been infected with malware, you’re on a ticking clock. This is one reason you should register your site with Google Search Console. If they detect malware on your site, they will email you, generally with the location and sometimes files that are causing the issue.
Don’t trust online website scanners. They often say a site is clean, because they perform a hasty, general scan, which doesn’t go very deep, where most malicious code is hidden. This is especially confusing when visitors see a red warning page that your site is hacked, or if you have received a warning that your hosting company is shutting you down for being hacked. Instead of placing your trust in an online scanners, let one of our security experts physically scan and check you site, and if it is hacked, they will uncover the infections!

Most people get hacked on sites like WordPress and Joomla because they won’t do their updates. If you’ve been hacked already, it’s too late to just update your way out of it. You need to have the vulnerability removed from the code of your site. There could be numerous back doors lurking in any number of files, allowing hackers to re-enter any time they like.
Here are the most common examples of website hacking, and while this is only a small sample of how you can tell if your site has been hacked, it should give you a good idea of what is going on with your website.
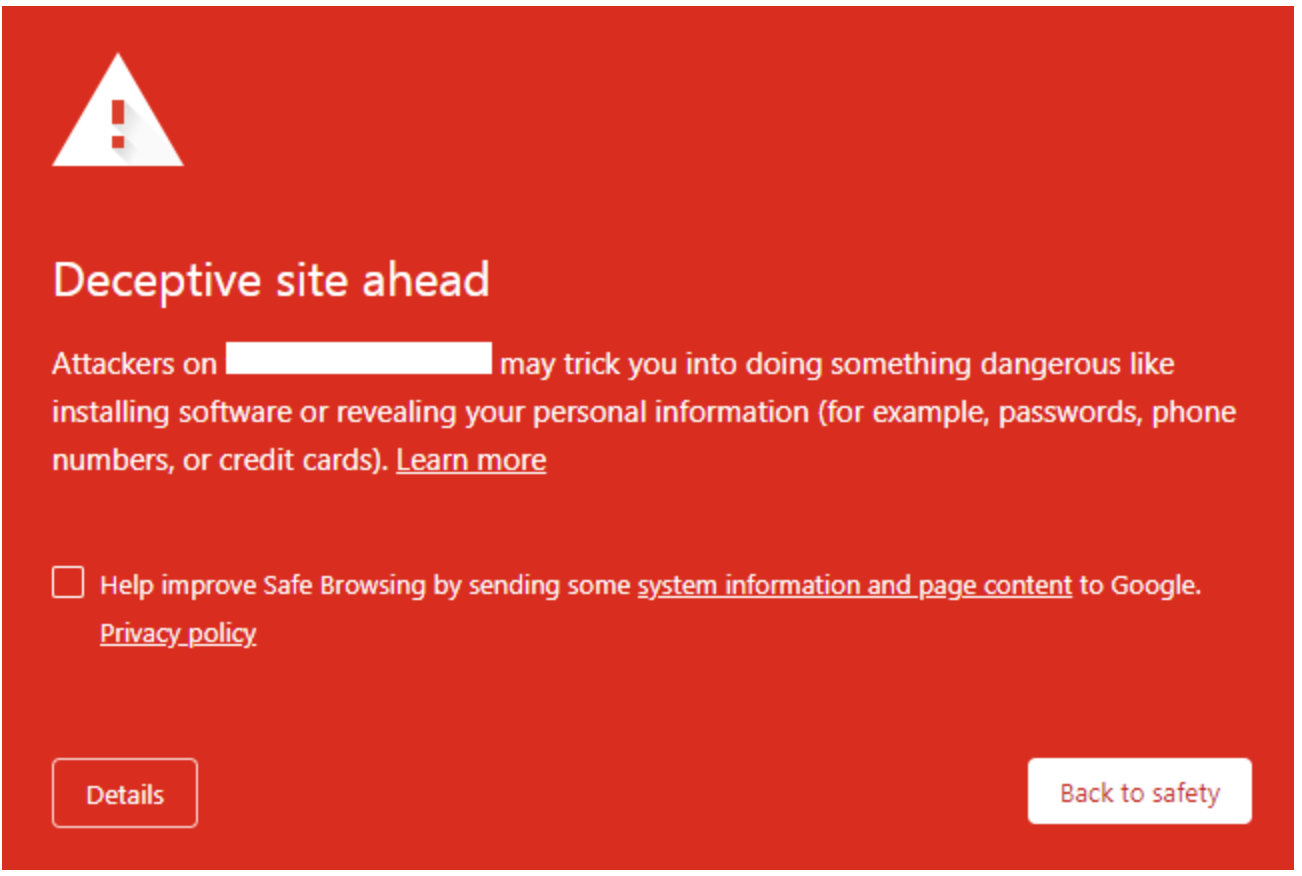
RED SCREEN WARNING:
The first way is you’ve been blacklisted by Google. You will see that through a red screen when you go to your website or you’ll see it in the Google search results. It might say “this site may be hacked”. So this is a good example of the red screen that you would see:
There’s a lot of other warnings out there that you’ll see from Google, but basically they’re all about the same. They mean the same thing: ‘Hey don’t go any further, you might get malware on your computer!’ You can see the same thing in the search results. It’ll say something like ‘this site may be hacked’, and if you click it, many times they’ll have a screen pop up that blocks it.
Sometimes you’ll see another message that says ‘this site may harm your computer’. Google puts that there to give website visitors a warning, and this is something that will actually destroy a business very quickly if you don’t take care of it. You need to remove the hack and you need to get rid of this warning.
WEBSITE REDIRECTS:
The next one is very common as well. It’s where your website redirects to a different site that you don’t own. Hackers are pretty smart. They won’t redirect it like on a desktop but they’ll redirect it if someone clicks your Google result on a cellphone, and they’ll redirect it to a porn site. For some reason they like to do it to churches. We know of dozens of churches that have had their websites hacked and redirected to porn sites.
HOSTING BAN:
Another way you know your site has been hacked is when your hosting company shuts you down. Many times you will see a screen warning that ‘this account has been suspended’. You will then get a very stern letter from whomever you’re hosting with, stating that if you don’t remove this malware they just won’t put your website back online. Then they try to get their partners to sign you up into these large ridiculous monthly plans that you don’t need. Our service, for instance, is a one-time fee, so in this type of situation you would have to remove the malware from the backend of your site first because you couldn’t access your site and use plugins or add content.
DEFACED HOMEPAGE:
Another giveaway that your website has been hacked is when your homepage is defaced. That basically means the hackers change your homepage for some religious or political message or just to say ‘hey your security is not where it needs to be’. This kind of hack is not really purely malicious; these guys could delete your site if they wanted to, but you know they’re just either trying to spread a message or they’re just trying to let you know of a security vulnerability. At the same time, it makes you look bad because you got hacked.
CAN'T LOG IN:
The next one is when you try to log into your WordPress site and you can’t log in. Hackers love to change passwords; they love to let you know they got the upper hand on you. Then when you’re trying to reset the password you never get the email because they obviously change the email as well.
HOSTING/EMAIL ISSUES:
You might see your hosting is using up too much resources or you know you’ve got something going on with your email.
ANTIVIRUS WARNINGS:
Sometimes you’ll get messages from your visitors, and they’ll share that norton antivirus popped up when visiting your site, and it said there was malware on your website. That’s another good indication that is something is going on. It might be on their computer but it’s definitely time to start looking to see if someone got into your site and put some malware on there.
SECURITY PLUGINS DISABLED:
Another one is if the security plugins get disabled on your site. After all, why would hackers want you to know your site is compromised? Now they can do whatever they want to do. Also when you’re looking around your site and you go to your users, especially in WordPress, and you notice there’s someone there that you didn’t add. You know it’s very common that hackers will leverage a user login so if you don’t even notice they will continue to wreak havoc.
STRANGE BACKLINKS:
The next example is when you’re looking around your site, checking out your content, and you notice there’s links on your website that you didn’t put there. SEO spam is very popular. People will hack into your site, put a link there, and then most people never notice it, but they might sell that link or use it for SEO purposes to steal the link juice from your site. So if you ever see links on your site that you didn’t put there–you got hacked.
In Summary
We hope this brief overview has helped you determine whether or not your site has been hacked. If you would like to know for sure, contact us here and we’ll take a look at the situation and recommend a solution to clean and protect it.
About Website Hacks: Viruses, Malware, Spyware, and More
Computer viruses, malware, spyware, Trojans, and worms. Are all these terms referring to the same thing?
The answer is technically no, they are different, and we’re going to go over what these differences are, whether it’s how they spread or what these things do to your computer. So maybe it’s just out of curiosity or it can help you protect your computer going forward.
The first term we can go over is pretty simple which is malware. This refers to any and all kinds of malicious software. It’s an all-encompassing term for any type of software that does harm to a computer. All the terms we’re going to be talking about could be considered malware. It’s like an umbrella term, but there are lots of suburbs so we’re gonna go over the different categories and types of malware, but when it comes down to it all malware usually has the same goal, which is to make money illegally for the creator of the malware.
The first type of malware we can talk about is a computer virus, which is usually the term that most people use all the time, but it’s not actually the most common type of malware. A computer virus is basically the name for malicious software that, when executed, replicates itself by modifying files for other programs and possibly the operating system itself. So that way, because these files are modified to now include the virus, whenever that program or the operating system is started, it will also run the virus code.
This could be for any number of reasons: stealing personal information, taking control of the computer, using its power or storage for something that the author of the virus wanted lots of…typical virus stuff you can imagine, but really the main design for a virus is that it remains dormant until it’s actually run by the user, and then when it is, it replicates itself in some way.
Virus files may come in the form of an .exe file which is executed directly, or perhaps it’s embedded in a macro in a Microsoft Word document or something like that, so when you run the program Microsoft Word, it exploits that and executes and then embeds itself in the rest of the computer that way.
So again downloading the file is not enough to infect your computer but once you do run it, presumably thinking it’s something else, then it does its virus thing, and it may spread itself by sending out an email to all your contacts the same way it was infecting you. Or maybe it puts itself in the upload folder for BitTorrent so then it also uploads itself to the file-sharing service so other people will download it something like that.
So the term virus has two qualities: it describes how it is spread, which is self-replication, and it’s also run manually by a user.
Now the next term might seem a bit similar and that is a computer worm. This also self replicates but it also has a very important difference in that–unlike a virus, which needs to be manually run by a user–a computer worm can spread itself automatically without user intervention. It doesn’t need a host program to run like MS word or the .exe file that you need to run. It can do this automatically. It basically scans for other computers on the network that it can infect and then it does so automatically if it’s able to.
Of course a worm will probably also have the ability to be run manually by user and infect computers that way. That might be how it initially gets started within a network and then spreads automatically from there. Worms actually spread using vulnerabilities and exploits of operating systems themselves to infect all the computers in a network. So once one computer is infected it scans all the other computers on network, sees if any other computers have that same vulnerability, and then it affects them automatically without any user transferring files or anything like that. It all happens automatically in the background from the virus itself.
If you’re wondering ‘Wait a minute, how can the worm spread to other computers if the user isn’t actually even running it?’ Well, it shouldn’t be able to and that’s why it is an exploit of a vulnerability. The operating system is not designed to work like that, but for whatever reason the worm is able to trick the operating system into not only downloading that file and the worm, but also running it with zero user intervention because of that exploit.
Now again the term ‘worm’ only describes the software, based on how it spreads and replicates, it doesn’t actually define what it does once it infects things. In fact, most computer worms don’t actually contain a so called ‘payload’, which is like side code that will do virus stuff that you typically think of, like spying on it or damaging the computer. So it might just spread just for the heck of spreading but that doesn’t mean that it won’t harm the network.
It still uses up CPU power and bandwidth and stuff like that but if it does happen to have a payload it could do any number of things that you typically associate with malware. Things like encrypting files for ransomware, spying, stealing credit card information, or installing a so-called backdoor, which might allow the computer to be controlled by the creator of the worm and then added into a botnet to do all sorts of malicious things as a group with other computers and worms.
This is just one more reason why you need to keep your operating system up-to-date because that’s just one example of software that can take advantage of exploits in your operating system. Usually older versions, after they’ve been discovered, and people don’t update, are a hackers dream. They can take advantage of these things and really it’s so easy to avoid–just keep your software up to date.
There are plenty of other types of malware that don’t replicate themselves but are just as destructive. The next type we can mention are Trojans or Trojan horses, which is a type of malware that misrepresents itself as a normal or benign program, but really it in the background will be doing malicious things. So it basically tricks the user into installing it because it thinks it’s something else.
It thinks it’s something legitimate and typically Trojans are the most common type of malware out there and they may actually look like real programs. They may run, they may do their intended purpose like if it’s a calculator app or something it might actually be able to calculate things and look like a calculator, but its main purpose is to get you to download it thinking it’s just a calculator. Then it does all this other stuff behind the scenes without you knowing.
Another really common example are fake antivirus programs that tell you ‘Oh look how many computer viruses and infections we found! You better buy our premium package to remove all these!’ When in reality that antivirus program itself is the virus. It’s fake. These Trojans can be spread in any number of ways that you can imagine such as spam email attachments that come out of the blue. They might be fake advertisements or through social media stuff, but again the main difference between the trojan and a virus is that a trojan doesn’t inject itself into files of other programs. It doesn’t replicate itself and send it to other people or anything like that. If it did it would be considered a virus.
So those three categories: viruses, worms, and Trojans typically describe the way that malware spreads, but they don’t talk about how much or necessarily what damage they do once they do infect.
The first of these is spyware which, just like the name suggests, is software or malware that spies on you or collects information from the computer and then sends it somewhere else. Now technically spyware could include programs that aren’t even illegal like you do give them permission to spy on you and collect information, but usually the vast majority of the time when someone says ‘spyware’ they’re referring to malware that did not get your permission to collect any information at all and is malicious.
Spyware could come in lots of different flavors: it could be a key logger which literally collects every single letter that you type in hoping to collect passwords or credit card numbers or bank accounts and stuff like that. It may also monitor what you’re doing online and monitoring your web traffic to be able to inject things into it such as advertisements, or maybe replacing links with affiliate links or advertisements to websites that it wasn’t necessarily going to direct to.
Usually malware that adds advertisements to your computer in one way or another is typically referred to as adware. So some of the malware that we talked about in this video may actually fall under multiple categories.
Another couple big categories are scareware and ransomware. Ransomware may be considered a subcategory of scareware. We’ll get to that, but scareware is typically some sort of malware that tricks a user into paying money or doing something by scaring them or threatening them. So one example might be a virus or a trojan or whatever that pops up on the screen that says you’re being arrested by the FBI unless you pay up this money as a fine or something like that. It scares you. It’s like ‘Oh no! I don’t want to get arrested!’, and then some people might actually pay. It may say if you don’t send this much Bitcoin to this address then the IRS is gonna arrest you and you’re gonna go to jail, but it doesn’t necessarily have to threaten you.
A lot of advertisements that are kind of sketchy–you’ve probably seen them–say your computer is infected with viruses, and to ‘click here’ to clean your computer…obviously it doesn’t know if your computer is infected or not it’s just trying to scare you into doing it. That would be scareware.
Now ransomware is a form of scareware that will typically hold your computer hostage in one way or another until you pay some amount of money. Sometimes ransomware may just be kind of bluffing and it only locks your computer in a way that’s pretty easy to reverse if you know you’re doing. It doesn’t actually affect any of your files.
Yet other times ransomware does have teeth and it actually will encrypt your files.
It says if you don’t pay us this amount of money within this amount of time we’re gonna destroy the decryption key and your files will actually be gone. The reason they do this is because, if people know that this particular software is out there and isn’t bluffing, then they’re a lot more likely to pay up to get their files back.
The final type of malware we’re going to explore is root kits. Root kits usually take over the computer by gaining elevated privileges or administrative privileges. The name rootkit comes from the term ‘root privileges’, which just means something that has control over the deepest, most secure parts of the operating system.
Because this type of malware does have such deep control over the computer it can hide itself very well. It literally has control over everything. It can even hide itself by not even including itself in the list of processes like in the task manager. This obviously means it’s going to be very very hard to remove, if not impossible, because it will even have control over the programs that are meant to remove it such as antivirus programs.
A root kit could prevent you from installing antivirus programs. It can stop antivirus programs from running stuff. Usually if you get a rootkit the best thing is to just completely wipe the drive and reinstall the operating system from scratch because you don’t know if you actually removed everything and if it’s actually still hiding and waiting to reinstall itself later. Root kits usually are able to install themselves using operating system vulnerabilities and exploits like we discussed earlier.
Now at this point you might be worried. There’s really three things you can do that will almost certainly protect you 99% of the time. The first of these is to keep your operating system and software up-to-date. Do not skip Windows updates. Update as soon as you get the ability to and you’ll be protected from any exploits.
The next thing is to backup your data. Have backup copies of your data, hopefully on a external hard drive that is not connected to the computer, so a ransomware can’t encrypt the backup as well. Or use something like cloud backup that is off-site this way if you do get malware that harms your files or does something else to your computer that requires a re-installation of your OS it’ll be way easier (and less expensive!) to recover them, especially in the case of ransomware.
Finally the third major thing is to use some sort of antivirus. It’s better than nothing to have the one that’s built into your computer such as Windows Defender, but ideally you use a type of antivirus that has thing called internet security which usually kind of scans for things coming across the network and can block things before they ever even get to your computer. Some of these antivirus programs also have anti ransomware features that will stop a program from running if it sees that it’s modifying files like ransomware might do.
If you’re looking for suggestions for some options for any viruses, one good option is BitDefender. ESET nod32 is another good one, but really you can just go on Google and search “best antivirus [current year]” and look at tests and see what one is the best for the current year.
So hopefully that clears things up if you didn’t know about the differences between names of other types of malware now you do. You should have a better understanding of how certain types of malware spread so you can better defend your computer against it.
If you think you’ve been hacked, and need help, get in touch with us here to discuss your options.
What is a SQL injection? Basically, it’s a way to attack websites that really shouldn’t work any more, but still does. SQL is a language in which you talk to databases and it’s fairly like English actually.
You can actually say things like, “Select from this table.” It’s not a complicated language. There are no great amounts of curly brackets and semi-colons and things like that. It can be, but you can pretty much type
commands in near English into it and you’ll get results back from your database.
This has existed for years, and that was all fine until the Web came along. Now people are looking at websites and are thinking, “These need to be hooked up to databases.”, because way back, when Tim Berners-Lee
invented the World Wide Web, it was pretty much “I’m gonna request a document and you’re gonna send that document back to me.” Eventually people worked out that what you really wanted to do was send a document and have different things come back, depending on what you sent.
Maybe you could type in a search request and that would go to a database and pull back something. That’s great, that’s brilliant, that’s a wonderful invention, and unfortunately, some programming languages did not deal with this in a sensible way.
One of the most notable ones that didn’t is a language called PHP. It’s a very easy language to write in. It’s a friendly language. I still haven’t met any other language that lets one develop code faster. It’s very fault-tolerant, within reason. It doesn’t always give you the best results when it does, but it’s friendly, easy to pick up, and crucially, you can just write it into a text file, upload it to a web server (in most of the world), and it will just work. You can type in PHP code and have it just run. So the barrier to entry is really, really low. Which makes web programming much more accessible.
Facebook was originally written in PHP. Innumerable things have originally been written in PHP and loads of things still are. WordPress still is. The trouble is, that if you’re not careful, there’s a lot of ways to go wrong. And this isn’t just PHP.
There are specific instances, that if you get it wrong just once, anywhere in your code, your web app is vulnerable. And if someone figures out that there’s a way in there, then good luck! Say goodbye to everyone’s passwords. There’s a lot more nasty stuff that can happen with SQL injections, but if your website has been hacked by a SQL injection and you need it fixed, get in touch with us ASAP and we’ll get it cleaned up for you.
Cleaning a site requires access to the admin area of your site, FTP login, and control panel access. After paying you will be redirected to a secure page to enter your login information that is sent encrypted to our systems. Only authorized Security Analysts have access to this information. We are not able to provide service for sites with certain configurations including those hosted on Windows servers. Additional charges may apply for sites over 10GB in size.